we are different
We are different. No commercial solution but only HW and SW components dedicated to E2EE transmission with Pre Shared OTP keys
We only use Hw that we are sure of that do not have back doors. We set them up so that only the parts of software that we need for our application are available. Additionally, our application runs only in RAM memory. We never store messages on disk

We are different in Server
Server exposed on Internet to execute transmission, and thus is prone to possible hacker attacks. For this reason, we have programmed it exclusively for transmission or reception of already encrypted messages. Unlike traditional servers, it does not store any information. es. It is not able to decipher messages.

We are different in Client
Our Client equiped with ARM CPUs it’s initialize with Secure Software for this reason there is no Back door. We never plan that the client has to connect directly to the Internet, but can only connect in WI-FI exclusively to its dedicated Server and to no other available WI-FI devices. Clien it’s able to encrypt and/or decrypt messages. They have pre-loaded OTP keys for each of the correspondents in the closed group they can talk to. They never store messages, operating only in RAM memory. Optionally, we have provided the ability to store messages at the user’s responsibility.
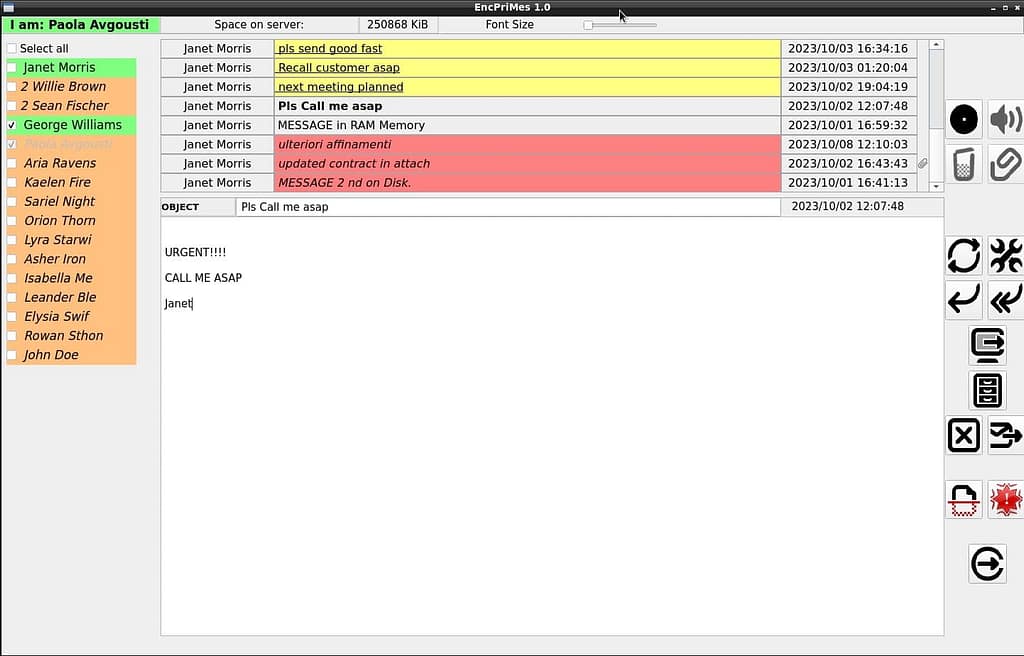
Software
Essential software, made to communicate only in an initially predefined group of correspondents. The complete list of correspondents is always present on the screen with an indication of their immediate or deferred reachability.
We manage also an outgoing message queue for each user. We transfer messages from Server RAM to Client RAM to be decrypted and presented unencrypted to the user. Default users can be given a new name such as Alias or Nikname to make them easily recognizable. Each message is listed with details of sender and other recipients in copy.
The sender, during the transmission phase, leaves no trace of the message; while messages received in memory are always removed when the client is turned off or alternatively voluntarily. The ability to add attachments will be added soon and they will be treated in the same way as the message itself, i.e., they will be encrypted along with the body and subject of the message.
