Priceless confidentiality in messages. The best-in-class software solution. Messages encrypted with OTP
Encrypted SMS on SmartPhone
Priceless privacy in messages
Protecting your privacy in the digital age

Fixed price solution
Each configuration purchased has a fixed price and has no additional hidden costs over time. The supply includes: Telephone, Encrypted SMS management software, Pre-shared long OTP KEY.

Tailor-made solution
Unique and non-reusable symmetric encryption key OTP (One Time Password). Configurations starting from 2 up to 250 pre-configured SmartPhones.

Priceless confidentiality in messages
Complete ownership of hardware and software: no intermediate third-party devices. Also resistant to brute force attacks carried out over time.

Address book configuration is required
The contact data is associated with the relevant Encrypted SmartPhone. Visual indication via lock and chat background.
E2EE ENCRYPTED SMS
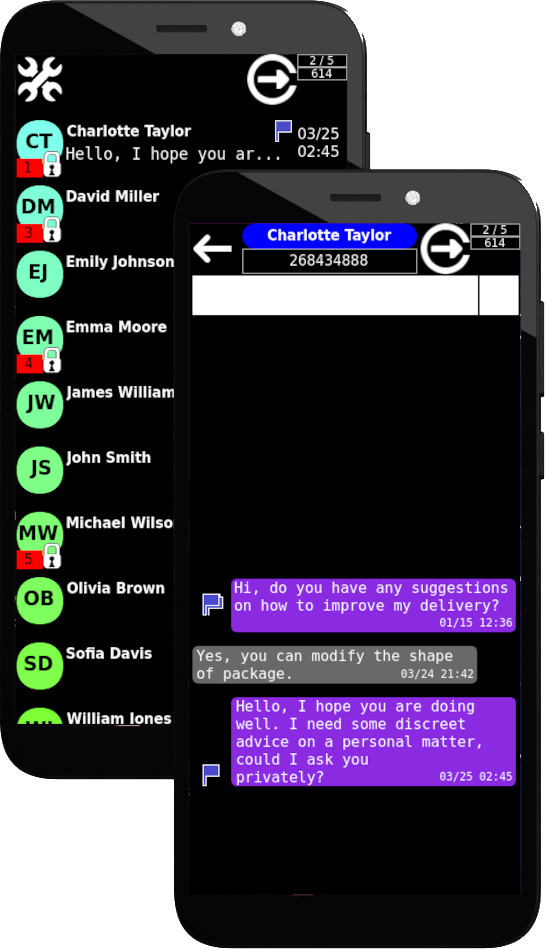
EncPriMes Private Chat SMS Message creates a confidential communication network. By selecting from your address book the users in possession of the Smartphone to and from which the encrypted messaging is used (highlighted with a closed padlock). It is possible to send these correspondents messages which will be transmitted in encrypted form. Only the recipient in possession of the encrypted telephone will be able to decipher the message which travels in encrypted form from the departure telephone to the arrival telephone E2EE.
OTP One Time Password
In cryptography, OTP is a password (keyword) used only once and never again. In addition to this, we immediately remove the password immediately after decoding the message, effectively eliminating the possibility that it will be possible to re-decipher the same message a second time after some time. Impossible to decipher the message if you are not the recipient; even in the event of interception by third parties, the message is indecipherable.
OTP One Time Pre-SHARED Password
Furthermore, our OTP password is always as long as the message, thus making the message indecipherable to anyone, even after some time and with brute force methods. No one will ever be able to decipher the message again in the absence of the key. All keys are pre-loaded into each device and are unique for each pair of phones and for each message direction (in and out)
Ephemeral MESSAGES
All SMS messages sent or received are never saved. They are only present in the SmartPhone’s memory if the phone remains turned on. When turned off, the messages are automatically removed and will never be available again. If the phone is NOT turned off, in any case it is possible to set a time for the automatic removal of messages older than a certain period of time which varies from 3 hours to 24 hours. In any case, it is possible to remove the single message voluntarily after selecting it.

SENDING AND RECEIVING CONFIRMATIONS
All encrypted SMS messages have sending and receipt confirmation (single or double flag). Each message sent is marked with a flag. After receiving and decrypting the plaintext message, a second flag returns to the sender indicating that the message has been received and converted into plaintext. In case of incorrect configuration of the message received by mistake from a telephone declared as encrypted but in reality this is not the case, a sequence of #?# characters is placed before the received message which indicates the anomaly to the recipient. Likewise, if a message is sent to a recipient declared to be encrypted, but in reality this is not the case, the message obviously remains in the encrypted state and no decryption confirmation is received. The recipient will receive an incomprehensible message.
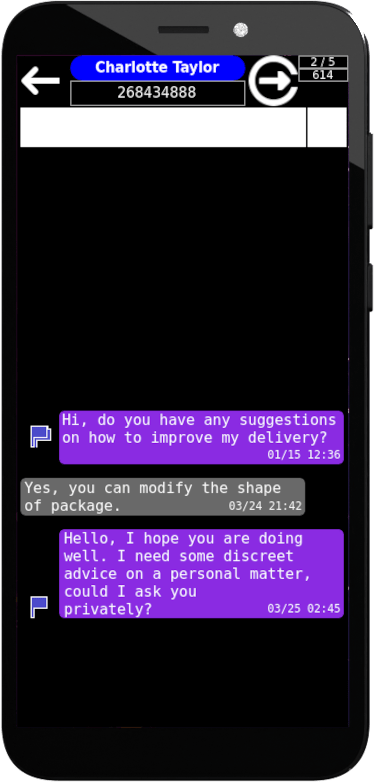
PHONE GROUP
All phones have an identification number of their number within the group. At the top right there is an indication of 2 / 5 (in the following image). This means that the phone is the second in a group of five. An incorrect association of the telephone number with the identification number of the telephone in the group will make the message sent incomprehensible to the recipient (and vice versa). Naturally, in the same way, phones belonging to different groups will not be able to communicate in encrypted form, but only with clear (unencrypted) messages.

ROBUST, RESILIENT, RESISTANT
Robust system that resists brute force attacks.
Resilient even to decryption attempts carried out after a long time.
Also Resistant to forensic analysis.
