
FAQ
The most commonly asked questions submitted by our users
What does this system allow ?
Our system enables secure transmission and receipt of correspondence in electronic format encrypted with OTP key. We use dedicated HW to do this. Additionally, End-to-end encryption is a security method that ensures the protection of communications. With End-to-end encryption, no one, can read messages as they travel between sender and recipient. Soon, the ability to include attachments, voice messages, videos, etc., will be activated.

How does it work ?
This system creates an anonymous and confidential communication network (OTP GROUP). This makes communication from and to others who are not part of it impossible.

Is the system reliable ?
Certainly. No one, not even those who designed it, will ever be capable of hacking encrypted messages.

Is the system independent ?
Certainly, this system is independent. There are NO Central Servers that third parties can turn off, disable, or control. The user is the only owner and responsible for his equipment and has full control over it.
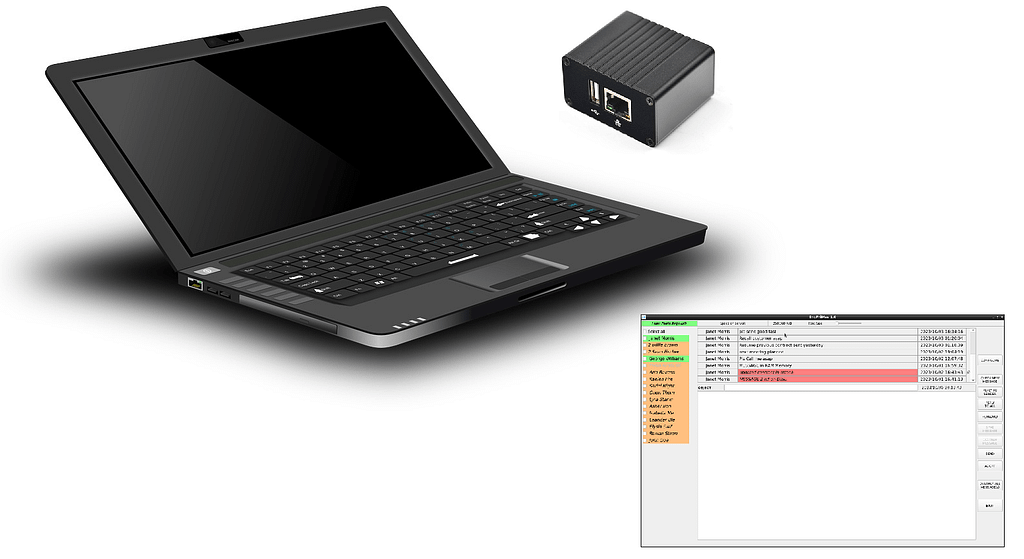
Can I later expand my initial configuration ?
NO. For security reasons, this architecture does not offer for KNOTS increase after activation. So, the customer decides the number of GROUP KNOTS at the time of ordering.

What happens if a KNOT fails ?
The mechanism for the part of the remaining non-faulted KNOTs will continue to work. So, the failed KNOT will be automatically excluded from it.

Is it possible to replace a KNOT ?
No. Since we do not have it’s original keys, we can’t replicate the KNOT itself.

How can I be informed of the available KNOTs ?
Each KNOT can list the other KNOTs in the network. It can highlight those that are active at that time. (Green/Light=reachable Orange=unreachable).
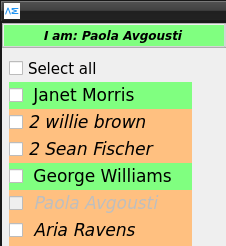
What happens if a KNOT is turned off ?
The sender KNOT holds the message in memory until the receiver KNOT is turned back on.
(Number) before Name means queued messages on unreachable User (Light Orange color)

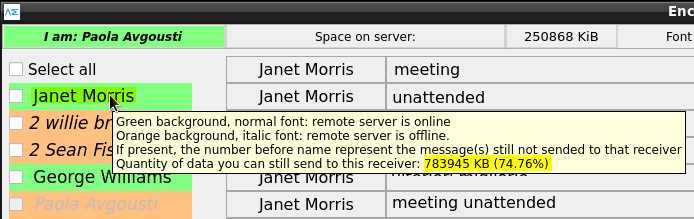
How am I informed of the remaining availability of keys for a transmission ?
This setup can report the remaining capacity of keys available for transmission. It does so well in advance of the end of the keys. The keys that can still be used are indicated for each recipient.
Hovering the pointer over the recipient activates a context tooltip message that displays related information.
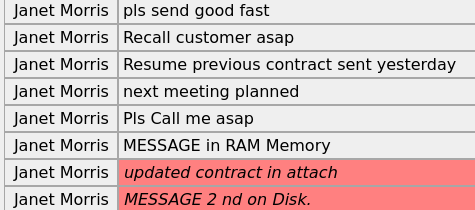
Who is in charge of storing transmitted messages ?
For security reasons, it merely conveys the message and is not responsible for storing it
on the device. Any saving of the message (and the resulting risk of copying) is the exclusive
responsibility of the user. (GREY=UNSAVED, RED=SAVED)
How can I remove the messages ?
Messages are sent and automatically removed from the source KNOT. This happens as soon as the intended device receives them. If I am the receiver, I can remove them voluntarily. In any case, ALL messages are removed when the KNOT is turned off (excluded eventually saved messages).

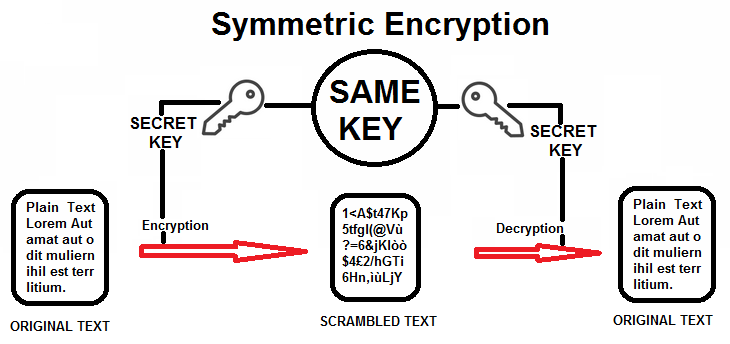
Are OTP messages encrypted?
In cryptography, OTP is an encryption technique that can’t be cracked. It requires a single-use pre-shared key. This key must be larger than or equal to the size of the message being sent. In this technique, a plaintext is paired with a secret key. Our Software EncPriMes use OTP pre-shared secret key.
How do I send an encrypted text message?
After purchasing at least one pair of Knots, connect the supplied server to the network and power it up. Then when the Notebook Client PC is turned on, start the EncPriMes program. Finally compose the message and select the Knot to send to. When you send the message, the platform EncPriMes will execute all the necessary operations to securely encrypt and send.
Can an OTP be decrypted?
If the key is random and never re-used, an OTP is provably unbreakable. Any ciphertext can be decrypted to any message of the same length by using the appropriate key. Thus, the actual original message can’t be determined from ciphertext alone, as all possible plaintexts are equally.

Can someone get my OTP?
In EncPriMes the OTP key is preloaded in the KNOT. Thus, there is no danger that someone can intercept it to make fraudulent or unauthorized use. The first message can’t be determined from ciphertext alone, as all possible plaintexts are equally.

What is the most secure way to send messages?
With EncPriMes you get the guarantee of utmost security. We use a system architecture that achieves the highest security available to date. In fact, the customer has sole ownership of all components of the transmission chain. This ownership ensures the message is sent to the recipient without it being read by others.
We use pre-shared symmetric key, end-to-end encryption, random OTP key, and backdoor-free hardware

How do I encrypt and decrypt text messages?
Enter any text to be Encrypted. Encrypt with a custom secret key. Enter Secret Key (Remember, the encrypted text can’t be decrypted without this secret key) Encrypted Output.
Send to selected KNOT/KNOTs of cryptograped message.
All tasks done by EncPriMes is completed

Didn’t find in our FAQ the answer you were looking for?
write us and we will help you overcome your doubts.

